Question #111
A Developer wants to encrypt new objects that are being uploaded to an Amazon S3 bucket by an application. There must be an audit trail of who has used the key during this process. There should be no change to the performance of the application.
Which type of encryption meets these requirements?
- A. Server-side encryption using S3-managed keys
- B. Server-side encryption with AWS KMS-managed keys
- C. Client-side encryption with a client-side symmetric master key
- D. Client-side encryption with AWS KMS-managed keys
Correct Answer: A
Reference:
https://docs.aws.amazon.com/AmazonS3/latest/dev/bucket-encryption.html
Question #112
An on-premises application makes repeated calls to store files to Amazon S3. As usage of the application has increased, “LimitExceeded” errors are being logged.
What should be changed to fix this error?
- A. Implement exponential backoffs in the application.
- B. Load balance the application to multiple servers.
- C. Move the application to Amazon EC2.
- D. Add a one second delay to each API call.
Correct Answer: A
Question #113
An organization is storing large files in Amazon S3, and is writing a web application to display meta-data about the files to end-users. Based on the metadata a user selects an object to download. The organization needs a mechanism to index the files and provide single-digit millisecond latency retrieval for the metadata.
What AWS service should be used to accomplish this?
- A. Amazon DynamoDB
- B. Amazon EC2
- C. AWS Lambda
- D. Amazon RDS
Correct Answer: A
Amazon DynamoDB is a fast and flexible NoSQL database service for all applications that need consistent, single-digit millisecond latency at any scale. It is a fully managed database and supports both document and key-value data models. Its flexible data model and reliable performance make it a great fit for mobile, web, gaming, ad-tech, Internet of Things (IoT), and many other applications.
Reference:
https://docs.aws.amazon.com/aws-technical-content/latest/aws-overview/database-services.html
Question #114
While developing an application that runs on Amazon EC2 in an Amazon VPC, a Developer identifies the need for centralized storage of application-level logs.
Which AWS service can be used to securely store these logs?
- A. Amazon EC2 VPC Flow Logs
- B. Amazon CloudWatch Logs
- C. Amazon CloudSearch
- D. AWS CloudTrail
Correct Answer: B
Reference:
https://aws.amazon.com/answers/logging/centralized-logging/
Question #115
A stock market monitoring application uses Amazon Kinesis for data ingestion. During simulated tests of peak data rates, the Kinesis stream cannot keep up with the incoming data.
What step will allow Kinesis to accommodate the traffic during peak hours?
- A. Install the Kinesis Producer Library (KPL) for ingesting data into the stream.
- B. Reduce the data retention period to allow for more data ingestion using DecreaseStreamRetentionPeriod.
- C. Increase the shard count of the stream using UpdateShardCount.
- D. Ingest multiple records into the stream in a single call using PutRecords.
Correct Answer: A
Reference:
https://aws.amazon.com/kinesis/data-streams/faqs/
Question #116
Where can PortMapping be defined when launching containers in Amazon ECS?
- A. Security groups
- B. Amazon Elastic Container Registry (Amzon ECR)
- C. Container agent
- D. Task definition
Correct Answer: D
Reference:
https://docs.aws.amazon.com/AmazonECS/latest/userguide/task_definition_parameters.html
Question #117
An application uses Amazon Kinesis Data Streams to ingest and process large streams of data records in real time. Amazon EC2 instances consume and process the data from the shards of the Kinesis data stream by using Amazon Kinesis Client Library (KCL). The application handles the failure scenarios and does not require standby workers. The application reports that a specific shard is receiving more data than expected. To adapt to the changes in the rate of data flow, the “hot” shard is resharded.
Assuming that the initial number of shards in the Kinesis data stream is 4, and after resharding the number of shards increased to 6, what is the maximum number of EC2 instances that can be deployed to process data from all the shards?
- A. 12
- B. 6
- C. 4
- D. 1
Correct Answer: C
Question #118
A Development team is working on a case management solution that allows medical claims to be processed and reviewed. Users log in to provide information related to their medical and financial situations.
As part of the application, sensitive documents such as medical records, medical imaging, bank statements, and receipts are uploaded to Amazon S3. All documents must be securely transmitted and stored. All access to the documents must be recorded for auditing.
What is the MOST secure approach?
- A. Use S3 default encryption using Advanced Encryption Standard-256 (AES-256) on the destination bucket.
- B. Use Amazon Cognito for authorization and authentication to ensure the security of the application and documents.
- C. Use AWS Lambda to encrypt and decrypt objects as they are placed into the S3 bucket.
- D. Use client-side encryption/decryption with Amazon S3 and AWS KMS.
Correct Answer: D
Question #119
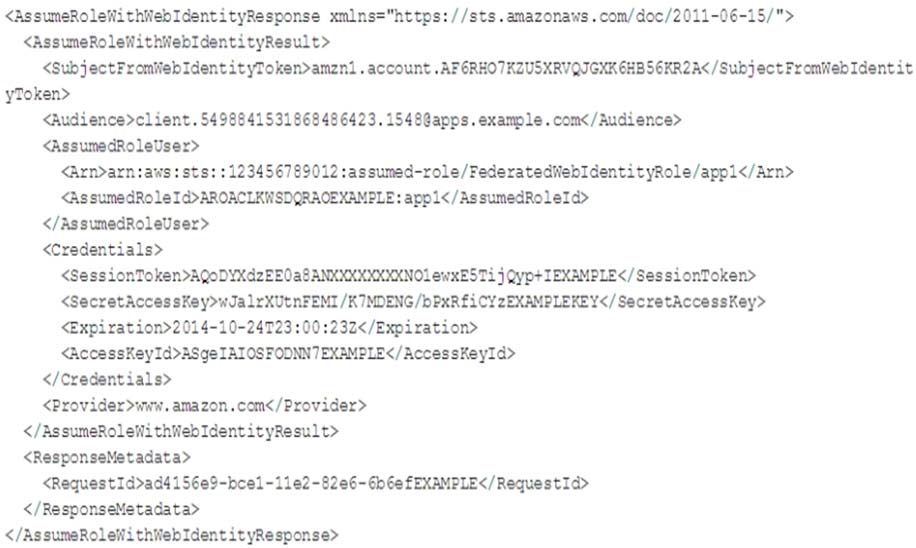
A company has an internet-facing application that uses Web Identity Federation to obtain a temporary credential from AWS Security Token Service (AWS STS).
The app then uses the token to access AWS services.
Review the following response:
Based on the response displayed what permissions are associated with the call from the application?
- A. Permissions associated with the role AROACLKWSDQRAOEXAMPLE:app1
- B. Permissions associated with the default role used when the AWS service was built
- C. Permission associated with the IAM principal that owns the AccessKeyID ASgeIAIOSFODNN7EXAMPLE
- D. Permissions associated with the account that owns the AWS service
Correct Answer: C
Question #120
A Developer is using AWS CLI, but when running list commands on a large number of resources, it is timing out.
What can be done to avoid this time-out?
- A. Use pagination
- B. Use shorthand syntax
- C. Use parameter values
- D. Use quoting strings
Correct Answer: A
Reference:
https://docs.aws.amazon.com/cli/latest/userguide/cli-usage-pagination.html