Question #51
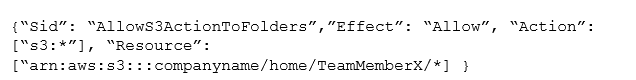
A development team consists of 10 team members. Similar to a home directory for each team member the manager wants to grant access to user-specific folders in an Amazon S3 bucket. For the team member with the username “TeamMemberX”, the snippet of the IAM policy looks like this:
Instead of creating distinct policies for each team member, what approach can be used to make this policy snippet generic for all team members?
- A. Use IAM policy condition
- B. Use IAM policy principal
- C. Use IAM policy variables
- D. Use IAM policy resource
Correct Answer: C
Question #52
A legacy service has an XML-based SOAP interface. The Developer wants to expose the functionality of the service to external clients with the Amazon API Gateway. Which technique will accomplish this?
- A. Create a RESTful API with the API Gateway; transform the incoming JSON into a valid XML message for the SOAP interface using mapping templates.
- B. Create a RESTful API with the API Gateway; pass the incoming JSON to the SOAP interface through an Application Load Balancer.
- C. Create a RESTful API with the API Gateway; pass the incoming XML to the SOAP interface through an Application Load Balancer.
- D. Create a RESTful API with the API Gateway; transform the incoming XML into a valid message for the SOAP interface using mapping templates.
Correct Answer: A
Question #53
A company is using AWS CodeBuild to compile a website from source code stored in AWS CodeCommit. A recent change to the source code has resulted in the CodeBuild project being unable to successfully compile the website.
How should the Developer identify the cause of the failures?
- A. Modify the buildspec.yml file to include steps to send the output of build commands to Amazon CloudWatch.
- B. Use a custom Docker image that includes the AWS X-Ray agent in the AWS CodeBuild project configuration.
- C. Check the build logs of the failed phase in the last build attempt in the AWS CodeBuild project build history.
- D. Manually re-run the build process on a local machine so that the output can be visualized.
Correct Answer: C
Question #54
A web application is using Amazon Kinesis Streams for clickstream data that may not be consumed for up to 12 hours.
How can the Developer implement encryption at rest for data within the Kinesis Streams?
- A. Enable SSL connections to Kinesis
- B. Use Amazon Kinesis Consumer Library
- C. Encrypt the data once it is at rest with a Lambda function
- D. Enable server-side encryption in Kinesis Streams
Correct Answer: D
Reference:
https://aws.amazon.com/about-aws/whats-new/2017/07/amazon-kinesis-streams-introduces-server-side-encryption/
Question #55
A developer wants to use AWS X-Ray to trace a user request end-to-end throughput the software stack. The Developer made the necessary changes in the application tested it, and found that the application is able to send the traces to AWS X-Ray. However, when the application is deployed to an EC2 instance, the traces are not available.
Which of the following could create this situation? (Select two.)
- A. The traces are reaching X-Ray, but the Developer does not have access to view the records.
- B. The X-Ray daemon is not installed on the EC2 instance.
- C. The X-Ray endpoint specified in the application configuration is incorrect.
- D. The instance role does not have “xray:BatchGetTraces” and “xray:GetTraceGraph” permissions.
- E. The instance role does not have “xray:PutTraceSegments” and “xray:PutTelemetryRecords” permissions.
Correct Answer: BE
Question #56
A Developer executed a AWS CLI command and received the error shown below:
What action should the Developer perform to make this error human-readable?
- A. Make a call to AWS KMS to decode the message.
- B. Use the AWS STS decode-authorization-message API to decode the message.
- C. Use an open source decoding library to decode the message.
- D. Use the AWS IAM decode-authorization-message API to decode this message.
Correct Answer: B
https://docs.aws.amazon.com/cli/latest/reference/sts/decode-authorization-message.html
Question #57
A company is using Amazon API Gateway to manage access to a set of microservices implemented as AWS Lambda functions. Following a bug report, the company makes a minor breaking change to one of the APIs.
In order to avoid impacting existing clients when the new API is deployed, the company wants to allow clients six months to migrate from v1 to v2.
Which approach should the Developer use to handle this change?
- A. Update the underlying Lambda function and provide clients with the new Lambda invocation URL.
- B. Use API Gateway to automatically propagate the change to clients, specifying 180 days in the phased deployment parameter.
- C. Use API Gateway to deploy a new stage named v2 to the API and provide users with its URL.
- D. Update the underlying Lambda function, create an Amazon CloudFront distribution with the updated Lambda function as its origin.
Correct Answer: C
Question #58
A company has written a Java AWS Lambda function to be triggered whenever a user uploads an image to an Amazon S3 bucket. The function converts the original image to several different formats and then copies the resulting images to another Amazon S3 bucket.
The Developers find that no images are being copied to the second Amazon S3 bucket. They have tested the code on an Amazon EC2 instance with 1GB of
RAM, and it takes an average of 500 seconds to complete.
What is the MOST likely cause of the problem?
- A. The Lambda function has insufficient memory and needs to be increased to 1 GB to match the Amazon EC2 instance
- B. Files need to be copied to the same Amazon S3 bucket for processing, so the second bucket needs to be deleted.
- C. Lambda functions have a maximum execution limit of 300 seconds, therefore the function is not completing.
- D. There is a problem with the Java runtime for Lambda, and the function needs to be converted to node.js.
Correct Answer: C
https://docs.aws.amazon.com/lambda/latest/dg/configuration-console.html
This is n old question, now the limit of execution extends to 900 sec or 15 mins.
https://aws.amazon.com/about-aws/whats-new/2018/10/aws-lambda-supports-functions-that-can-run-up-to-15-minutes/
Question #59
An application stops working with the following error: The specified bucket does not exist. Where is the BEST place to start the root cause analysis?
- A. Check the Elastic Load Balancer logs for DeleteBucket requests.
- B. Check the application logs in Amazon CloudWatch Logs for Amazon S3 DeleteBucket errors.
- C. Check AWS X-Ray for Amazon S3 DeleteBucket alarms.
- D. Check AWS CloudTrail for a DeleteBucket event.
Correct Answer: D
https://docs.aws.amazon.com/AmazonS3/latest/dev/cloudtrail-logging.html
Question #60
An organization must store thousands of sensitive audio and video files in an Amazon S3 bucket. Organizational security policies require that all data written to this bucket be encrypted.
How can compliance with this policy be ensured?
- A. Use AWS Lambda to send notifications to the security team if unencrypted objects are pun in the bucket.
- B. Configure an Amazon S3 bucket policy to prevent the upload of objects that do not contain the x-amz-server-side-encryption header.
- C. Create an Amazon CloudWatch event rule to verify that all objects stored in the Amazon S3 bucket are encrypted.
- D. Configure an Amazon S3 bucket policy to prevent the upload of objects that contain the x-amz-server-side-encryption header.
Correct Answer: B
https://aws.amazon.com/blogs/security/how-to-prevent-uploads-of-unencrypted-objects-to-amazon-s3/





Thank you !!
Helped me in achieving my aws developer certification.